Phone
07905 240254Phone
07905 240254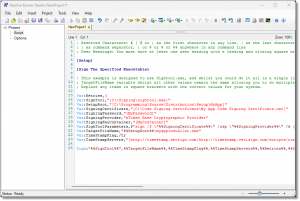 With effect from 1st June 2023 a whole new set of Code Signing Requirements came into effect. Created by the CA/Browser Forum, this move is designed to counter the big increase in stolen certificates being used to introduce malware into trusted applications.The result of this is that all publicly trusted Certificate Authorities (CA) now require that in order to obtain a code signing certificate a certified hardware security module (HSM) meeting at least FIPS 140-2 level 2 or Common Criteria EAL 4+ must be used to protect the code signing private keys. This requirement applies to both Organisation Validation (OV) and Extended Validation (EV) certificates.
With effect from 1st June 2023 a whole new set of Code Signing Requirements came into effect. Created by the CA/Browser Forum, this move is designed to counter the big increase in stolen certificates being used to introduce malware into trusted applications.The result of this is that all publicly trusted Certificate Authorities (CA) now require that in order to obtain a code signing certificate a certified hardware security module (HSM) meeting at least FIPS 140-2 level 2 or Common Criteria EAL 4+ must be used to protect the code signing private keys. This requirement applies to both Organisation Validation (OV) and Extended Validation (EV) certificates.
This means that many applications that include code signing funcitonality are now broken, with no clue when or even if they will be repaired. We use some of this software, and we want to continue to use it, so how do we solve the problem? Simple really, we added a new Sign command and let Pipeline Runner do it for us! Of course, that won’t break the old way of doing it using the Exec command if you prefer.
The Sign command allows you to run any digital signing application that can be run from the command line from within the script. Examples of programs that you might want to run include the ubiquitous Microsoft Signtool.exe, EZSignit, and so on. One key feature of this command is to allow a list of timestamp servers to be specified. These will be tried sequentially until successful or the number of retries is exceeded. This function reduces the number of times a pipeline run fails due to an error returned by a timestamp server by spreading the load and ensuring that there is a gap between the retries on each server which could be seen as abusive if they happen too quickly.
IMPORTANT: The function of this command is to run third party code signing tools. As a result if you need support on the syntax required by any application you should contact the support team of the product developer. We are unable to offer support for third party applications of which we have no knowledge and over which we have no control.
For more details and sample code see the command documentation at https://pipelinerunner.com/docs/commands-sign.html